Toronto Cybersecurity Services
Network Security Services Provider for Toronto and Surrounding Areas
The threats are real. Having strong cyber security protection is important.
Long gone are the days when all you needed was a decent firewall and an up-to-date virus scanner to protect your systems. Cybercrime is a big business. The number of players including nation states is increasing and the tools available to launch attacks are inexpensive and readily available. Small- to mid-sized companies are prime targets as they often do not have the resources to allocate to cybersecurity in Toronto, but, clearly, something has to be done.

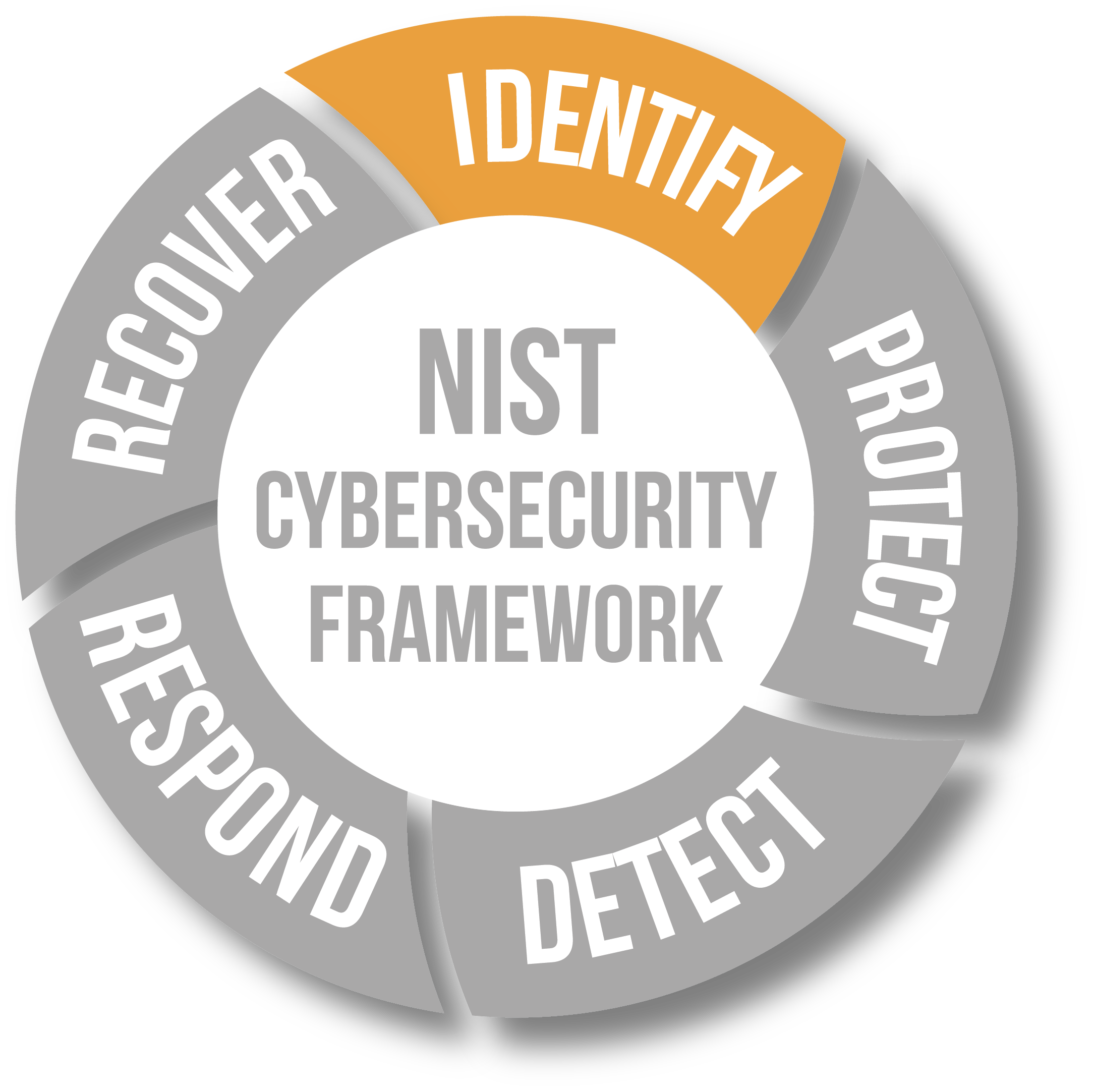
Following the NIST Cybersecurity Framework is a great place to start.
Why Choose XBASE for Cyber Security Solutions?

Following the NIST Cybersecurity Framework is a great place to start.
As a reputable cybersecurity company in Toronto, XBASE Technologies believes the NIST Cybersecurity Framework is the best place to begin. The five areas shown here are the basis for effective managed cybersecurity monitoring for SMBs, and XBASE provides support and solutions for each segment.
The time is now. Move up to “Exponentially Better™” Cyber Security with XBASE:
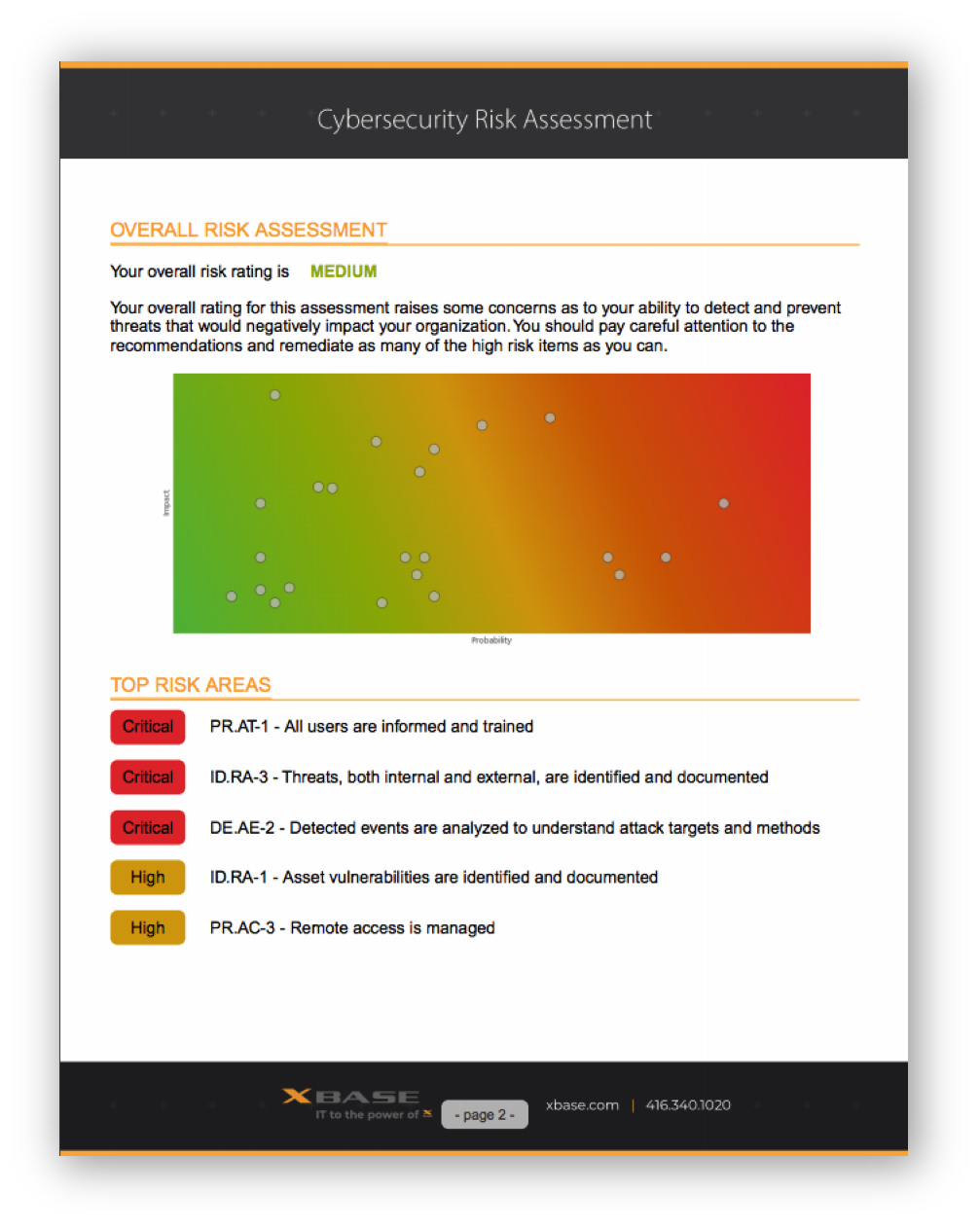
NIST Risk Assessment
XBASE will help you complete a NIST Cybersecurity survey to help find the security areas that require focus. Answers collected here will help drive you through the Cybersecurity Circle, and as we work with you on improvements, you can revisit the survey to show improvements.Security Awareness Training & Phish Testing
The most effective defense against malware and phishing attacks is knowledge. The more your staff know about cybersecurity issues, the less likely they are to become victims. As part of our Managed cybersecurity monitoring for SMBs, XBASE has partnered with KnowBe4, a leader in Security Awareness Training, and can offer our clients online training and testing on a wide range of subjects including malware, ransomware, social engineering, management of sensitive information, PCI, and mobile device security. XBASE will work with you to choose a training plan for your staff and help you get it running.
CrowdStrike
XBASE provides CrowdStrike for all of its managed services and security network monitoring clients. CrowdStrike is an industry leader in the field of endpoint protection providing advanced malware detection and prevention for servers and workstations.Intrusion Protection
XBASE provides advanced IPS (Intrusion Protection) services designed to prevent attacks on your infrastructure. IPS Systems perform web content filtering and zero-day malware blocking services by inspecting your internet traffic and searching for known bad patterns. Many malware attacks are blocked by these services because they prevent the malware from getting started in your network.System Patching
Most exploits take advantage of unpatched systems, with the 2017 WannaCry cryptolocker variant being a great example. Microsoft and other vendors release updates and security patches whenever vulnerabilities are found in their products, but if you are not updating your systems in a timely manner, you are exposing your company to avoidable risks. XBASE manages security patch deployments for all our managed services clients to ensure that systems are kept up to date and are not vulnerable to known exploits. XBASE also runs regular scans on networks to identify and remediate systems that may be at risk, and we bring these to client’s attention via our monthly reporting and live dashboards as part of our network monitoring.Whole Disk Encryption for Laptops
If you have users with laptops, then you may be at risk of data loss. Regardless of company policies in effect, mobile users tend to store work files on the local drives of their laptops for a variety of reasons. This may include confidential corporate or client information, financial or personal information. The theft or loss of a laptop may expose your company to liability. XBASE can provide centrally managed, whole disk encryption service. While you may not get your lost laptop back, you can be assured that no one has access to any of the data that may have been stored on the system.Email Protection
The biggest threats from malware and phishing attacks lives in your inbox. Users are lured into clicking on attachments or hyperlinks, or to responding to fabricated requests by cyber criminals. XBASE’s premium mail security program dramatically reduces the risk of a bad email in your inbox by replacing attachments with sanitized copies guaranteed to be free of malware or scripts, quarantining questionable senders and replacing dangerous hyperlinks with secure tested links. By proactively keeping the bad email out of your users’ inboxes, we eliminate email as the source for ransomware and other dangerous malware. XBASE email protection is available for both on premises Exchange and Office 365 (O365) online Exchange.Two Factor Authentication
Another aspect of our managed cybersecurity services in Toronto is the fact that XBASE provides fully managed two factor authentication services designed to protect users accessing mail, cloud applications, VPNs, and other services. When logging into a service, the user will supply their user ID, password AND will need to have access to their mobile phone to authenticate. Two factor authentication is an effective way to prevent password sharing and brute force password attacks against your important systems.
Intrusion Detection
XBASE provides advanced IDS (Intrusion Detection) services that monitor traffic on your network in real time looking for known types of attacks or suspicious activities. Malicious traffic will be blocked, with resulting alerts being investigated by our network operations team. IDS is effective against zero-day exploits as well as command & control malware.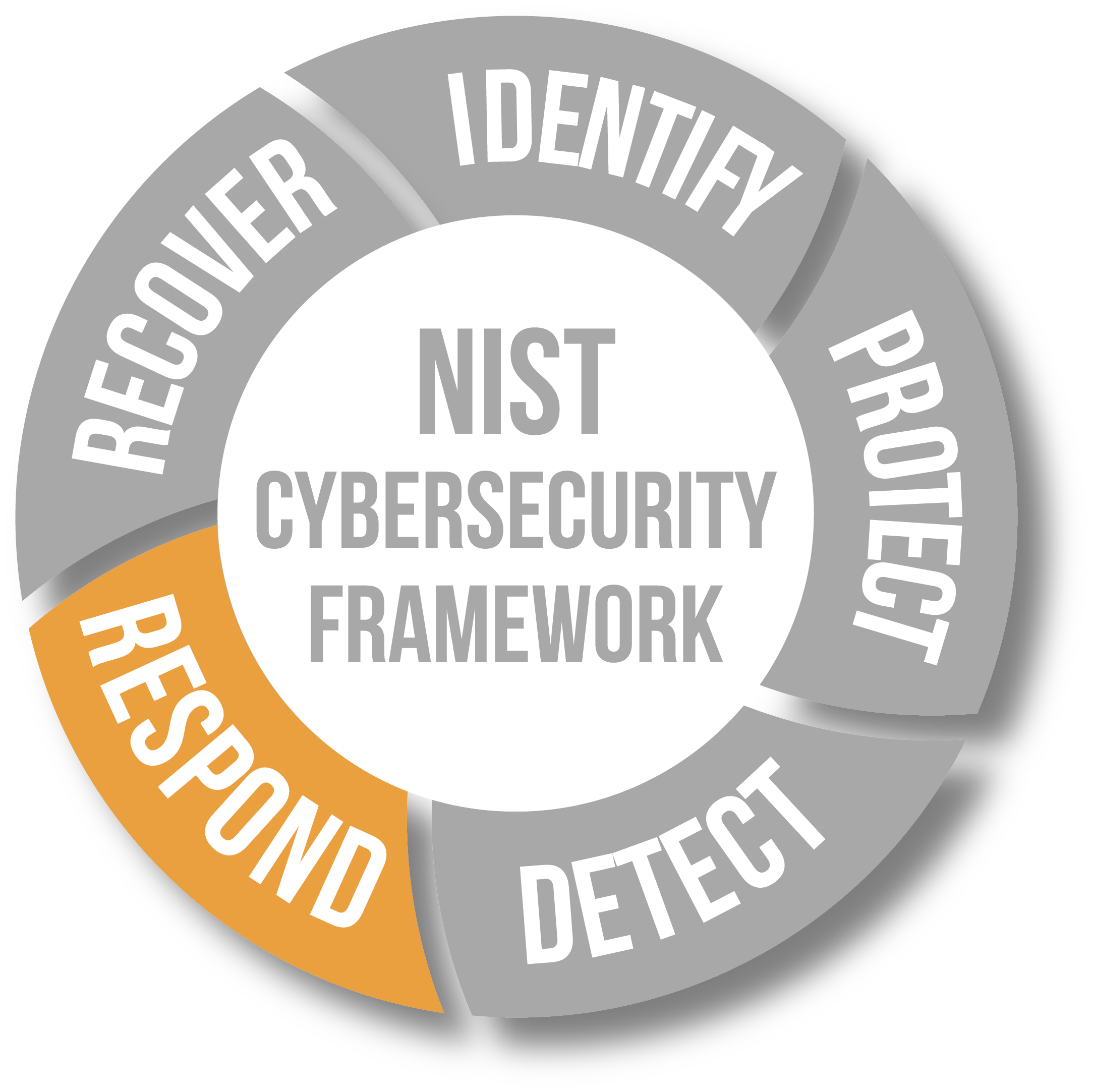
XBASE: Your rapid response team
It's not enough to hope you’re not hit with a breach or hack. XBASE’s managed cybersecurity monitoring for SMBs begins with helping you put together an Incident Response Plan, while at the same time establishing a comprehensive response framework to address known attacks:- Use of Managed Network devices to quickly isolate network segments when issues are found
- Customer notification systems (email and SMS), escalation lists and documented contacts available
- Availability of Forensic resources
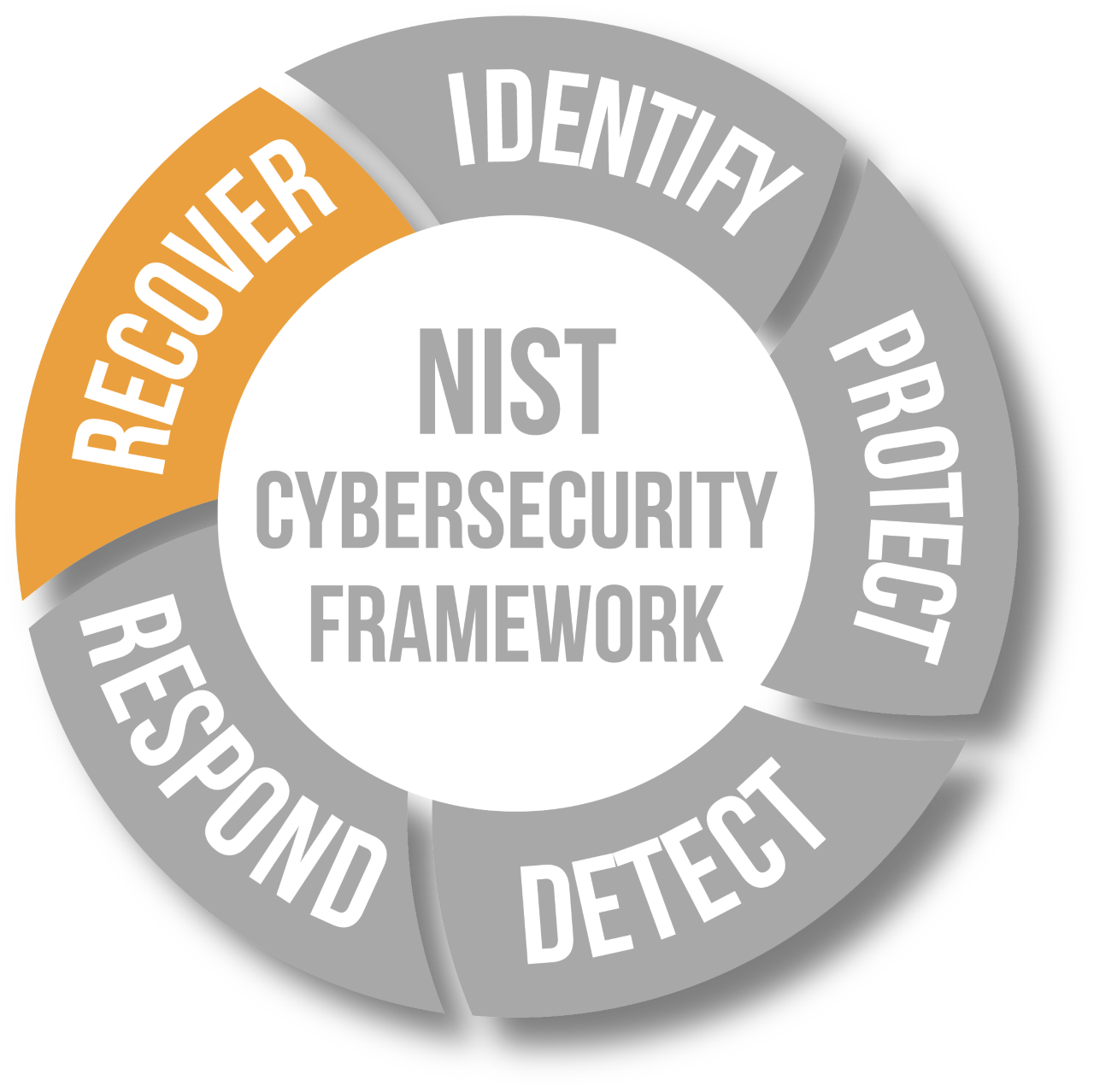
Backup and Disaster Recovery Services
In the battle against cybercrime the final line of defense is having solid backups. With the volume of new exploits and malware releases happening daily, even the best detection and prevention systems can be beaten. You need to know that your backups are reliable and that when all else fails, you can ensure your recovery. XBASE provides fully managed and monitored remote backup and disaster recovery services. We confirm backups daily and have regularly scheduled test restores and D/R tests to ensure recoverability.Cyber Security Insurance
Whether it's for compliance reasons or simply for peace-of-mind, cybersecurity insurance in Toronto is becoming a valuable part of the recovery plan, providing much-needed funds to quickly and effectively regain IT operational status. XBASE can work with you to source and review an appropriate cybersecurity insurance policy, plus provide comprehensive documentation at the time of claim.Still unsure? Consider the following:
- It takes 191 days, on average, for unprotected organizations to identify a data breach
- $6 million is the average cost of a cybersecurity breach of a Canadian company
- 4 million malware files and 9 million malware URLs per month were blocked by Panda software in 2018, a 60% increase from the previous period
- 92% of malware is delivered by email, and over half of IT decision-makers cite “phishing” attacks as their top security threat
- 40% of medium to large organizations are targeted by “RDP” (Remote Desktop Protocol) attacks, capitalizing on improperly protected services when employees connect to their computers remotely
- The rise of “remote code execution” attacks, 90% of which are used to hijack your computers for bitcoin mining or “cryptojacking” – a 350% increase over the previous period
- 77% of compromised attacks are “fileless” or “zero-footprint” – where existing software is exploited and nothing new is installed on the user’s computer

You must be logged in to post a comment.